https://cve.circl.lu/comments/feedMost recent comments.2025-12-23T17:30:14.182450+00:00Vulnerability-Lookupinfo@circl.lupython-feedgenContains only the most 10 recent comments.https://cve.circl.lu/comment/21f63dda-f998-4c51-b7ce-6efc09015c56A vulnerability report for BYD (Chinese car maker)2025-12-23T17:30:14.188493+00:00Cédric Bonhommehttp://cve.circl.lu/user/cedric
# Vulnerability Report - BYD QIN PLUS DM-i - Dilink OS - Incorrect Access Control
**Product:** BYD QIN PLUS DM-i - Dilink OS
**Vendor**: https://www.byd.com/
**Version**: 3.0_13.1.7.2204050.1.
**Vulnerability Type:** Incorrect Access Control
**Attack Vectors**: The user installs and runs an app on the IVI system that only requires normal permissions.
## Introduction
The BYD QIN PLUS DM-i with Dilink OS contains an Incorrect Access Control vulnerability. Attackers can bypass permission restrictions and obtain confidential vehicle data through **Attack Path 1**: **System Log Theft** and **Attack Path 2**: **CAN Traffic Hijacking**.
## Attack Path 1 : System Log Theft
Incorrect access control in BYD QIN PLUS DM-i Dilink OS 3.0_13.1.7.2204050.1 allows unaithorized attackers to access system logcat logs.
### Description
The DiLink 3.0 system’s /system/bin/app_process64 process logs system logcat data, storing it in zip files in the /sdcard/logs folder. These logs are accessible by regular apps, allowing them to bypass restrictions, escalate privileges, and potentially copy and upload sensitive vehicle data (e.g., location, fuel/energy consumption, VIN, mileage) to an attacker’s server. This poses a serious security risk, as the data is highly confidential for both users and manufacturers.
### Detailed Steps
1. Check the system-collected and stored system logs.
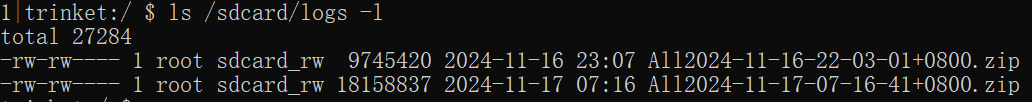
2. The malicious app copies system files to its own private directory. The main code is as follows:
<img src="https://s2.loli.net/2025/01/26/EqxHDSX9O5Ibhr4.png" alt=".png" style="zoom: 50%;" />
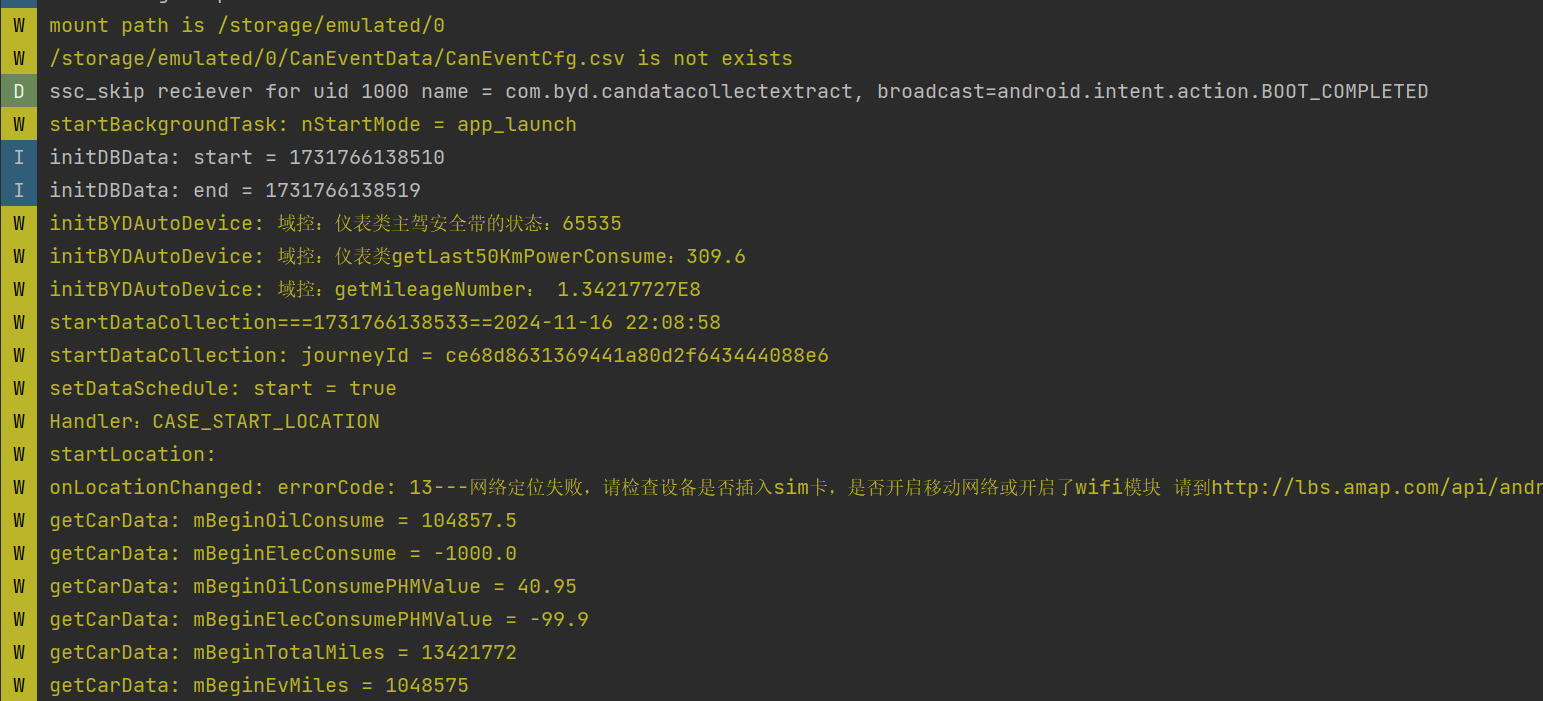
3. The malicious app successfully steals system logs to its private directory.
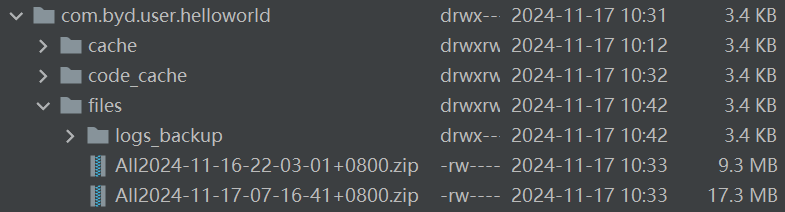
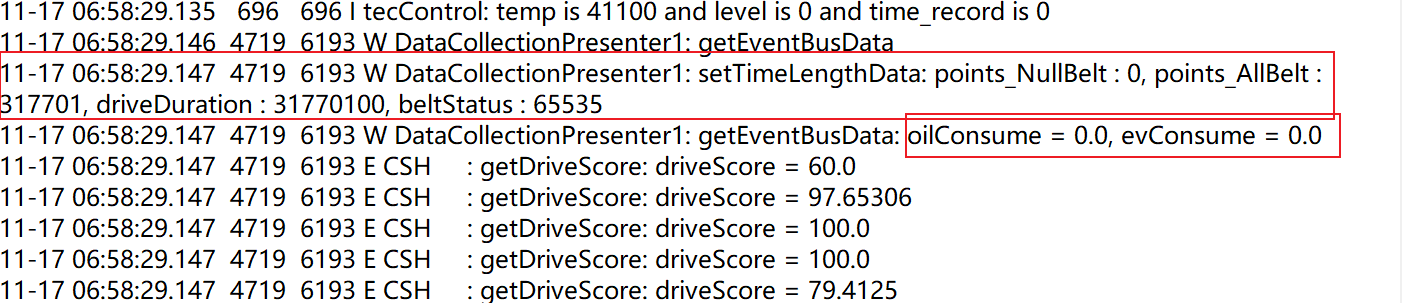
4. Extract the file and search for sensitive confidential information in the system logs.
(a) Fuel consumption, energy consumption, and seatbelt status.
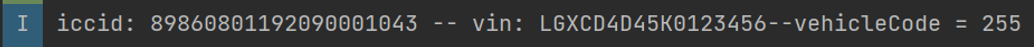
(b) ICCID, VIN (Vehicle Identification Number), and model code.
(c) Diagnostic command format.

(d) Various detailed vehicle status information.
### **Ethical Considerations**
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in in the latest versions, with the logs now encrypted.
### Additional Notes
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
### Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.
## Attack Path 2 : CAN Traffic Hijacking
The attacker can remotely intercept the vehicle's CAN traffic, which is supposed to be sent to the manufacturer's cloud server, and potentially use this data to infer the vehicle's status.
### Description
In the DiLink 3.0 system, the /system/priv-app/CanDataCollect folder is accessible to regular users, allowing them to extract CanDataCollect.apk and analyze its code. The "com.byd.data_collection_notify" broadcast, not protected by the system, lets apps set the CAN traffic upload URL. This enables attackers to:
1. Set the upload URL to null, preventing cloud data collection.
2. Set the upload URL to an attacker’s domain for remote CAN traffic collection.
Additionally, the encoded upload files can be decrypted using reverse-engineered decoding functions, enabling attackers to remotely analyze CAN traffic and infer the vehicle's status.
### Detailed Steps
1. The vulnerability code for the broadcast handling in CanDataCollect.apk.
<img src="https://s2.loli.net/2025/01/26/RanvVwJZYUuq9i8.png" alt=".png" style="zoom:50%;" />
2. The exploitation code for the malicious app vulnerability.
<img src="https://s2.loli.net/2025/01/26/QBC8cxEkKtuY5XT.png" alt=".png" style="zoom:50%;" />
3. The malicious app successfully modifies the uploaded CAN traffic URL.
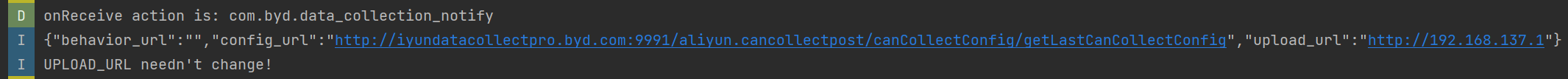
4. After the attack on the IVI system, the logcat logs route CAN traffic to the attacker’s server.
<img src="https://s2.loli.net/2025/01/26/2Cxtc3UvFe9X7pn.png" alt=".png" style="zoom: 50%;" />
5. The CAN traffic collected by the attacker and the decoded results.
<img src="https://s2.loli.net/2025/01/27/YqinPrht6S8CFBW.png" alt=".png" style="zoom:50%;" />
### **Ethical Considerations**
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in the latest versions.
### Additional Notes:
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
### Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.2025-01-26T17:57:50.934368+00:00